
VP and Head of Software Operations ICT Division, Bank Asia Ltd.
What is Cybersecurity?
Cyber: Relating to, or involving computers or computer networks.
Cyber Security: The safeguard taken to avoid or reduce any disruption from an attack on data, computers or network devices.
Many definitions regarding Cybersecurity in google search:
- Cybersecurity entails the safeguarding of computer networks and the information they contain from penetration and from malicious damage or disruption.
- Cyber Security involves reducing the risk of malicious attack to software, computers and networks. This includes tools used to detect break-ins, stop viruses, block malicious access, enforce authentication and enable encrypted communications.
- Cybersecurity is the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that can be used to protect the cyber environment and organization and user’s assets.
- The body of technologies, processes, practices and response and mitigation measures designed to prcyber-managmentotect networks, computers, programs and data from attack, damage or unauthorized access so as to ensure confidentiality, integrity and availability.
Security Basics:
From the above definitions, IT Security can be categorized into anumber of ways:
- Computing Security
- Applications Security
- Information Security
- Network Security
- Database Security
Computer Security: We continuously use computers to process and to keep valuable data. Many IT services like Data Entry, Printing documents, File transferring, Video conferencing, Accounting and many more are operated by these computers. Computer security means these services provided by the computers are protected from unintended or unauthorized access, change or destruction.
Computers can be a subject and/or an object of an attack.
When the subject of an attack, a computer is used as an active tool to conduct the attack.
When the object of an attack, a computer is the entity being attacked.A Case Study of Computer Security:
A pay order issued fradulantly from a Sundry Account at branch of a ABCD Bank:
Audit team identified that a Payorder issued fradulently by user ‘A’ from sundry creditor accout where the beneficiary was his colleugue ‘B’.
After an investigations audit team identified that the pay order was cashed at other bank account by clearing transactions where holder account was ‘B’.
‘B’ was caught and disclosed that he was issued that payorderfavouring his account using user ‘A’ machine while ‘A’ went for lunch without shutdown his machine.
‘B’ was accessd his machine through remote access system and made the transactions.
Applications Security:
We are developing several software applications to make our business process faster and more accurate. These applications are used for record keeping and communications with other networks users.
Application security encompasses measures taken throughout the application’s development life-cycle to prevent exceptions when run live.
Adequate risk mitigations measures should be taken at the time of design, development, deployment, upgrade, or maintenance of the application.
A Case Study of Applications Security:
Applications Developed for Internet banking facility: User has rights to transfer funds only to their registered accounts where user can select destinations accounts from the list.
After six years of running the system a customer who was also a programmer found no validations at the final stage when inserting data in the database.
The customer taking this opportunity to change the destinations account to his account and source account by predicting some accounts. After some attempts he transferred some amounts from different accounts to his account.
Information Security:
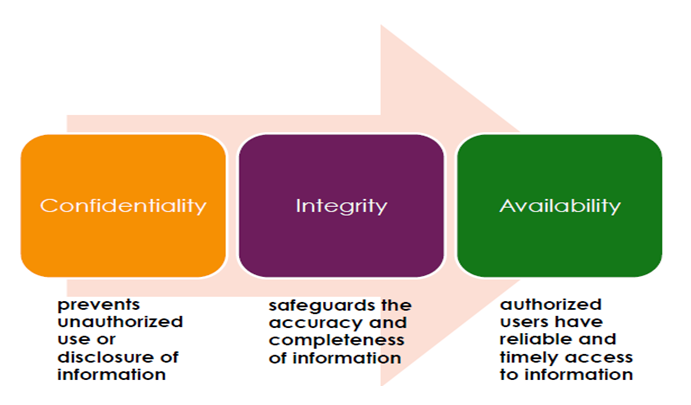
The main objectives of information security is CIA: confidentiality, integrity, and availability.
Confidentiality:
Confidential information should not be accessible to unauthorized users. That is, messages sent by X to Y should not be readable by Z. A good example of methods used to ensure confidentiality is an account number or routing number when banking online.
Data encryption is a common method of ensuring confidentiality. User IDs and passwords constitute a standard procedure; two-factor authentication is becoming the norm. Other options include biometric verification and security tokens.
Integrity:
Ensuring that data may only be modified by authorized means. Integrity involves maintaining the consistency, accuracy, and trustworthiness of data over its life cycle.
Data must not be changed in transit, and steps must be taken to ensure that data cannot be altered by unauthorized people.
Availability:
Authorized users should be able to access data when they need data.
Main Goals of Information Security are:
What is Network Security?
Computer networks, both public and private, are used every day for transactions and communications among businesses, government agencies and individuals.
The networks are linked by communication systems some of which might be private, such as within a company, and others which might be open to public access.
Network security refers to activities designed to protect your network. Specifically, these activities protect the usability, reliability, integrity, and safety of your network and data. Effective network security targets a variety of threats and stops them from entering / spreading on your network.
An effective network security strategy requires identifying threats and then choosing the most effective set of tools to combat them.
Cyber Threats:
Cyber threats typically consist of one or more of the following types of attacks:
- Phishing
- Trojans
- Ransomware
- Wiper Attacks
- Data Destruction
- Spyware/Malware
- Man in the Middle (MITM)
- Drive-By Downloads
- Malvertising
- Unpatched Software
Phishing:
Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by an electronic communication.
Fake website similar to original where if you put your user name and password it sends this information to the hacker.Afterwards it redirects to original website to divert you.
Trojans
A Trojan horse or Trojan is a type of malware. Trojans can be employed by cyber-thieves and hackers trying to gain access to users’ systems. Users are typically tricked by some form of social engineering into loading and executing Trojans on their systems. Once activated, Trojans can enable cyber-criminals to spy on you, steal your sensitive data, and gain backdoor access to your system. These actions can include:
Deleting data
Blocking data
Modifying data
Copying data
Disrupting the performance of computers or computer networks
Unlike computer viruses and worms, Trojans are not able to self-replicate.
How Trojans can impact you
Trojans are classified according to the type of actions that they can perform on your computer:
- Backdoor
A backdoor Trojan gives malicious users remote control over the infected computer. They enable the author to do anything they wish on the infected computer – including sending, receiving, launching and deleting files, displaying data and rebooting the computer. Backdoor Trojans are often used to unite a group of victim computers to form a botnet or zombie network that can be used for criminal purposes. - Rootkit :
Rootkits are designed to conceal certain objects or activities in your system. Often their main purpose is to prevent malicious programs being detected – in order to extend the period in which programs can run on an infected computer. - Trojan-Banker:
Trojan-Banker programs are designed to steal your account data for online banking systems, e-payment systems and credit or debit cards.
Ransomware
Ransomware is a form of malicious software that, once it has taken over your computer, threatens you with harm, usually by denying you access to your data. The attacker demands a ransom from the victim, promising — not always truthfully — to restore access to the data upon payment.
Users are shown instructions for how to pay a fee to get the decryption key. The costs can range from a few hundred dollars to thousands, payable to cybercriminals in Bitcoin.
Ransomwarecanaccess a computer in many ways. One of the most common delivery systems is phishing spam — attachments that come to the victim in an email, masquerading as a file they should trust. Once they’re downloaded and opened, they can take over the victim’s computer, especially if they have built-in social engineering tools that trick users into allowing administrative access.
Social engineering is the art of gaining access to buildings, systems or data by exploiting human psychology, rather than by breaking in or using technical hacking techniques. For example, instead of trying to find a software vulnerability, a social engineer might call an employee and pose as an IT support person, trying to trick the employee into divulging his password.
Case Study Social Engineering:
A bank teller was asked by anIT person to deposit inanother branch account for testing:
IT officer calledabranch teller that there was a problem with one account:When entering the amount400029 taka it gave anerror. Please test it and after sometime you reverse it.
Teller was convinced and made the transaction and waited for IT person’s feedback. After some time teller found no response from the IT person and reversed the transactions.
The account owner informed branch manager that they delivered goods to their customers as per this deposit.
Security Attacks:
The three goals of information security- confidentiality, integrity, and availability – can be threatened by security attacks.
There are three groups of attacks based on the security goals. These are:
1. Attacks Threatening Confidentiality
– Snooping
It refers to unauthorized access to data or interception of data.
For example, a file transferred through the internet may contain confidential information. An unauthorized entity may intercept the transmission and use the contents for her own benefit.
How to Achieve Message Confidentiality?
To achieve message confidentiality or privacy, the message must be encrypted at the sender’s site and decrypted at the receiver’s site.
To provide message confidentiality with symmetric-key cryptography, a sender and a receiver need to share a secret key.
2. AttacksThreateningIntegrity
– Modification
– Masquerading
– Replaying
– Repudiation
Modification
After intercepting or accessing information, the attacker modifies the information to make it beneficial to herself.
Sometimes the attacker simply deletes or delays the message to harm the system or to benefit from it.
For example, a customer sends a message to a bank to do some transaction. The attacker intercepts the message and changes the type of transaction to benefit herself. It means that the attacker intercepts the message and changes it.
Masquerading
Masquerading or spoofing happens when the attacker impersonates somebody else. For example, an attacker might steal the bank card and PIN of a customer and pretend that she is that customer.
Sometimes the attacker pretends to be the receiver entity. For example, a user tries to contact a bank, but another site pretends that it is the bank and obtains some information from the user.
Replaying
Replaying means the attacker obtains a copy of a message sent by a user and later tries to replay it.
For example, a person sends a request to her bank to ask for payment to the attacker, who has done a job for her. The attacker intercepts the message and sends it again to the bank to receive another payment from the bank.
Repudiation
It means that sender of the message might later deny that she has sent the message; the receiver of the message might later deny that he has received the message.
This type of attack is different from other attacks because it is performed by one of the two parties involved in the communication: the sender or the receiver.
An example of denial by the sender could occur when a customer asked her bank to send some money to a third party but later denied that she has made such a request.
An example of denial by the receiver could be when a person buys a product from a manufacturer and pays for it electronically, but the manufacturer later denies having received the payment and asks to be paid.
3. Attacks Threatening Availability
Denial of service
Denial of service (DoS) is a very common attack. It may slow down or totally interrupt the service of a system.
The attacker can use several strategies to achieve this. For example,
- The attacker might send so many bogus requests to a server that it crashes because of the heavy load.
- The attacker might intercept and delete a server’s response to a client, making the client believe that the server is not responding.
- The attacker may also intercept requests fromclients, causing the clients to send requests many times and overload the system.
Easy some ways to Prevent Cyber Attacks
Even if we don’t currently have the resources to bring in an outside expert to test our computer systems and make security recommendations, there are simple, economical steps we can take to reduce our risk to be a victim to a costly cyber-attack:
- Train employees in cyber security principles.
- Install, use and regularly update antivirus and antispyware software on every servers & computers used in your business.
- Use a strong firewall system to protect any DoS attack.
- Download and install software updates for operating systems and applications as they become available.
- Make backup copies of important business data and information.
- Control physical access to our computers and network components.
- Secure your Wi-Fi networks. If you have a Wi-Fi network for your workplace make sure it is secure by password protection.
- Require individual user ID for each employee.
- Limit employee access to data and information and limit authority to install software.
- Use complex password and regularly change passwords.
Cyber Attacks have no ends To be continued……..








